Using AWS Secret Manager for Credential Management Service
AWS provides AWS Secret Manager Service for easier management of secrets. Secrets can be database credentials, passwords, third-party API keys, and arbitrary text. Secrets Manager is used to replace hardcoded credentials in the code, including passwords, with API calls to Secrets Manager to retrieve the secret programmatically.
For more information on how to modify password properties to use with credential management systems, see Using Credential Management Service for Properties of Type Password .
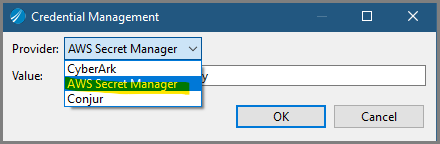
A new AWS Secret Manager provider is added for the Credential Management for property of type password.
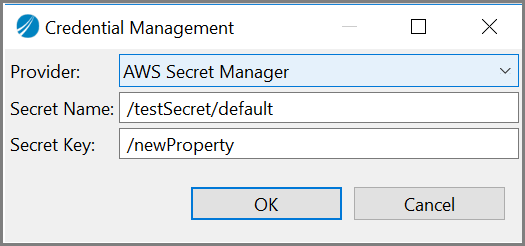
The AWS Secret Manager has two fieldsǰ Secret Name and Secret Key. In the Secret Name and Secret Key fields , add the secret name and secret key that is to be retrieved from the AWS secret manager.
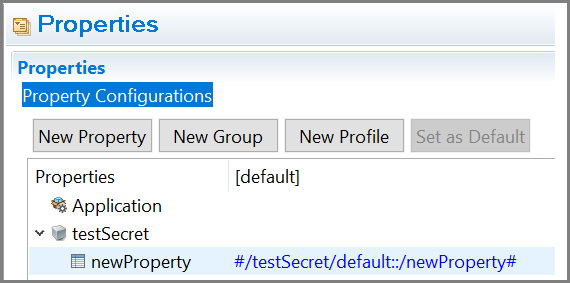
On the AWS systems manager console or using AWS CLI, the password properties need to be stored in the AWS secret manager. The recommended format is to have secret name as /<applicationModule_name/<profile_name>. This makes sure that the property names are unique within the AWS secret manager as well as within the application. However you can use other names. The recommended format is using secret key as the /<property_name>.
For example, #/testSecret/default::/newProperty#.
Following are the steps to use AWS Secret Manager for Secrets Management Service:
To set the engine variables for your application in TIBCO Cloud™ Integration, refer Adding Custom Properties section in the Configuring App Properties topic.
Integrating ECS and EKS Services with AWS Secret Manager
Support for credential management service for AWS Secret Manager is provided while deploying application on ECS and EKS services.
Set the environment variables APP_CONFIG_PROFILE and AWS_SECRET_MANAGER to configure ECS and EKS services with AWS Secret Manager.
To use AWS Secret Manager with EKS service for passwordless solution, deploy the application on an EKS cluster configured to a service account, OIDC provider, and an IAM role associated with the cluster, pass the environment variables APP_CONFIG_PROFILE and
AWS_SECRET_MANAGER. The AWS credentials do not need to be passed. For more information, see https://aws.amazon.com/it/blogs/opensource/introducing-fine-grained-iam-roles-service-accounts/